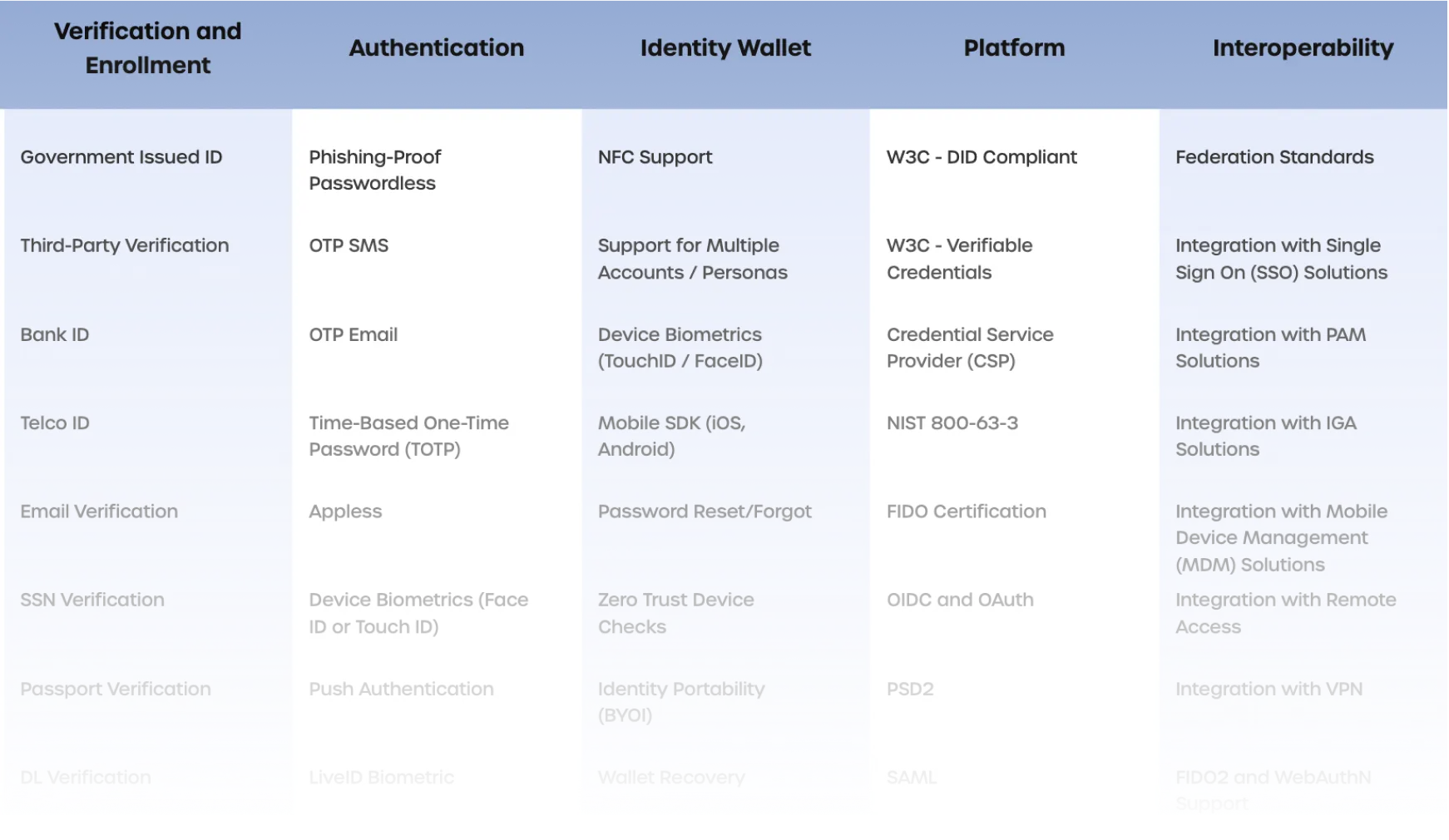
Our Advantage
The 1Kosmos Workforce Advantage

User Experience and Satisfaction
When it comes to signing into the corporate VPN or accessing business applications, the manner in which users prefer to log in can be as diverse as the workforce itself.
To achieve both security and a positive user experience, it’s ideal to tailor the authentication experience to the needs of the business and to individual preferences, which makes it important to have the ability to implement multiple authentication methods (even provide coexistence with previous technologies) to reduce friction while still ensuring a high level of security.
Some users would opt for device-level biometrics, others would prefer scanning a QR code. Certain categories of workers might be required to use a live selfie to prove liveness. Still, others will take time to wean themselves off user ID, passwords and old-fashioned 2FA codes.
Passwordless MFA for Diverse IT Environments
While unverified trust is one of the key reasons organizations fail when taking a bolt-on approach to passwordless multi-factor authentication, many organizations struggle with a patchwork approach including 2FA, SSO and legacy systems across hybrid and remote environments.
What is need is a cost-efficient passwordless strategy not only for newer IT systems but also to deal with legacy, non-federated applications that can’t go passwordless (e.g., Unix, Mainframe, Linux). Here, the major platform providers have made strides, but not without limitations. 1Kosmos provides passwordless MFA across diverse IT environments.


Security and Interoperability
NIST 800-63-3, FIDO2, ISO27001 and iBeta ISO/IEC 30107-3 are contemporary technical standards designed to ensure security and interoperability for biometric authentication and passwordless access. Certification to these standards indicates that the solution has passed rigorous testing to validate that they are developed to the highest quality standards.
Certification helps prevent security loopholes and vendor locks from proprietary or otherwise closed technologies that can tie organizations to expensive renewal and maintenance contracts. Adopting technologies that have out-of-the-box connectors, open APIs, and a robust SDK can ensure long-term interoperable solution viability and improve return on investment by reducing OPEX.
Flexible Levels of Identity Assertion
For certain employees or classes of workers organizations sometimes require higher levels of authentication, such as requiring two-factor authentication for contractors and employees with privileged access to critical systems or for executives with signature authority. Matching the authentication method to the risk associated with the access event will provide the level of security and convenience appropriate to the access request.


Privacy and Compliance
Distributed ledger technology goes beyond the public-private key security that comes with a FIDO2 and NIST certified solution to provide additional security by eliminating administrative access to centralized “honeypots” of user personal information. In this unique approach, information is sharded, encrypted and then stored in a private blockchain. The locations of those blocks of information are then encrypted and stored to provide an additional security layer protecting the integrity of any digital assets, in this case a decentralized digital identity.
This architectural advantage creates an immutable audit trail, meaning events are logged in perpetuity and cannot be manipulated, giving IT a detailed and indisputable picture of all changes to identity and access attempts for auditors and to meet Zero Trust requirements for user authentication.
Explore the capabilities that make the 1Kosmos platform your best friend
See the key capabilities