The Challenge
Privileged credentials are the targets of choice for hackers. The reason is that privileged accounts are the gateway to an organization’s most sensitive IT infrastructure, including DevOps, critical systems, and applications. This is why the perpetrators of some of the highest profile breaches have leveraged mismanaged or unmonitored privileged accounts. Moreover, the management of privileged access is a necessity and highly complex, given the mix of cloud, hybrid, and on-premise environments and the myriad of human and service accounts involved.
81 percent of hacking-related breaches are the consequence of stolen and weak passwords (2018 Verizon Data Breach Report). This means that an admin who leverages a password at any point during the authentication process to access a privileged account is vulnerable to identity compromise. Also, let’s keep in mind that with a 2FA solution or a Password-based MFA solution, an individual’s password, the first authentication factor, can be stolen and is a prime target for phishing attacks. Therefore, the user shouldn’t know nor manipulate a password to access a privileged account.
Passwordless MFA solutions that involve basic biometrics as a factor of authentication do not ensure the security of your key systems and applications. For example, fingerprint recognition like Touch ID and facial recognition like Face ID do not identify the person using the phone, since multiple fingers/faces can be registered on a single smartphone.
Finally, the addition of security features to protect the access to privileged accounts oftentimes means heightened friction for the user and consequently a frustrating experience.
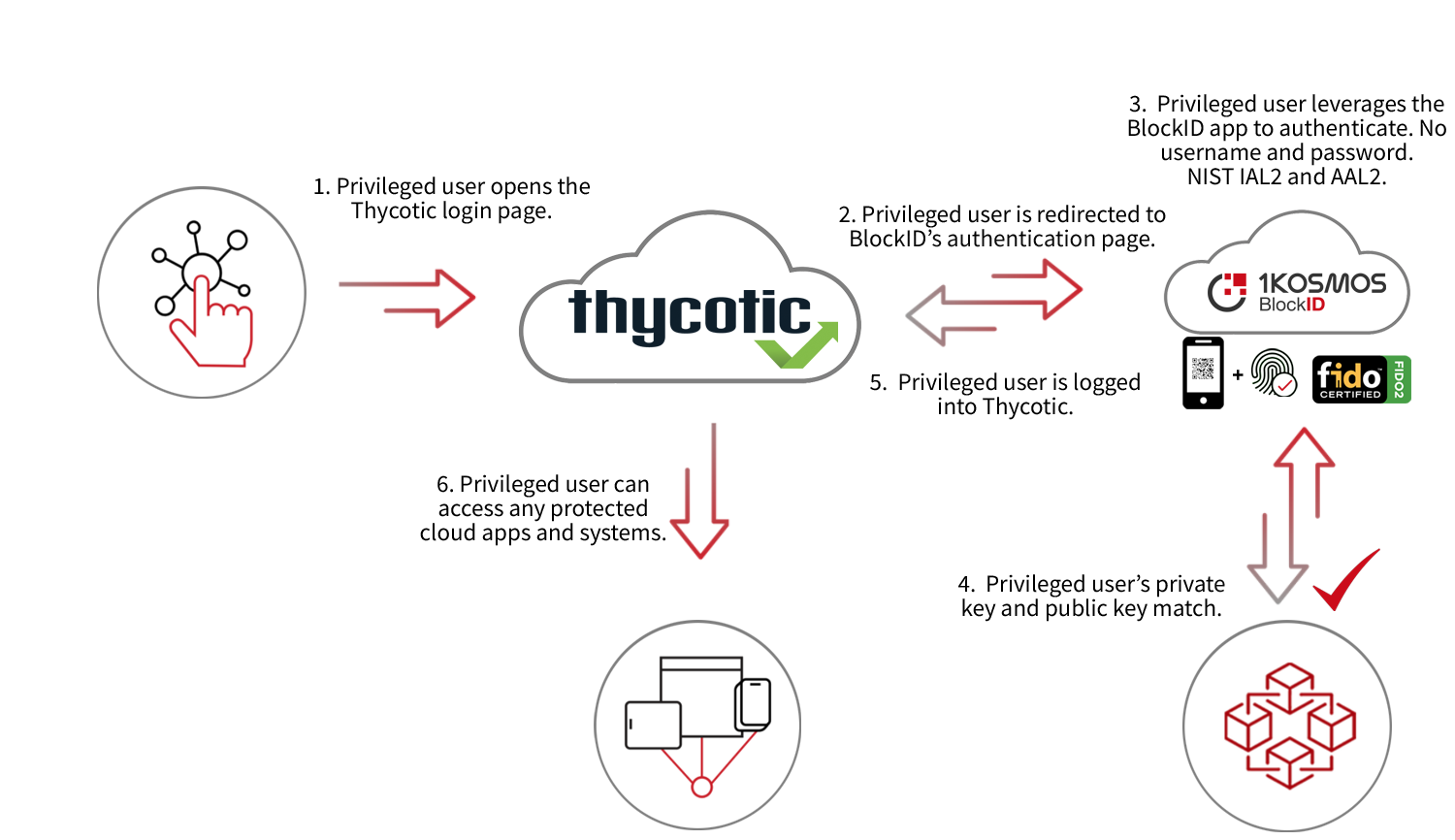
Identity-Based Authentication for Thycotic: