What Is 3FA (Three-Factor Authentication)?
How secure are you in a world where data breaches and cyber-attacks make headlines daily? You might think you’re doing enough if you’ve already upgraded to Two-Factor Authentication (2FA). However, the cyber world and its threats are evolving—enter Three-Factor Authentication (3FA). This enhanced security protocol adds an extra layer of armor, making unauthorized access even more complex. In this comprehensive guide, we dive deep into the what, why, and how of 3FA, providing insights that can help you bolster your cybersecurity posture.
The Foundations of 3FA
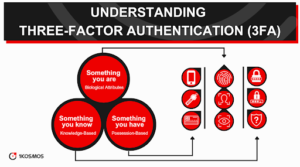
What is 3FA?
Three-Factor Authentication (3FA) is a security protocol that adds an extra layer of protection on top of the traditional Two-Factor Authentication (2FA). 3FA requires users to present three identifying factors before accessing an account, app, or system.
This knowledge factor could involve something the user knows (password), something the user has (a used mobile phone or device), and something the user is (biometric data).
The concept behind 3FA is straightforward: The more the three authentication factors are involved, the harder it is for unauthorized users to gain access. It’s an example of a comprehensive approach to security that makes extra steps in the verification process more robust by reducing the chances of a breach.
The Evolution from 2FA to 3FA
Two-factor authentication (2FA) has been the industry standard for securing accounts, stolen passwords, and systems. However, as cyber threats grow in sophistication, there is an increasing need for more rigorous security measures.
3FA evolved as a response to this need, incorporating an additional layer of security beyond password, making it even more difficult for unauthorized users to access accounts.
This third layer could be various things, such as a fingerprint scan, a biometric identifier, or a behavioral pattern. It depends on the system in the security question and its security requirements. By adding this additional layer, 3FA significantly raises the bar for attackers trying to compromise a system.
Who Needs to Know About 3FA?
3FA is increasingly relevant to a broad audience. Organizations dealing with sensitive or classified information are generally considered the most obvious candidates for 3FA.
This includes governmental agencies, healthcare institutions, government agencies, and financial firms. However, any organization bolstering its cybersecurity posture can benefit from implementing 3FA.
Moreover, individual users with a heightened need for security, such as celebrities, businesses, or public figures, can also benefit from 3FA. Even the general public is beginning to appreciate more advanced security protocols as awareness of cyber threats grows.
How Does 3FA Work?
The mechanics of 3FA are a natural extension of 2FA, with the difference being the additional inherence factor of a third factor for validation. Like 2FA, the user must provide two forms of identification and a third, distinct type of identity-confirming credentials for verification.
The 3FA Process Explained
Typically, 3FA starts with the user entering a username and a password. Next, a secondary device, like a smartphone, receives a time-sensitive code.
After entering this code, the user or phone must provide a third form of identification: a fingerprint or retina scan, a voice recognition test, or some other form of biometric verification. Only after successfully passing through all three gates does the user gain access to the system or account.
Types of Factors in 3FA
The factors used in 3FA usually fall into at least one element of three categories: knowledge-based (something you know), possession factor-based (something you have), and inherence-based (something you are).
Knowledge-based factors include passwords and PINs, possession-based factors encompass mobile devices or smart cards, and possession and inherence-based elements refer to biometrics like fingerprints or iris scans.
Different combinations of these categories can be employed depending on the level of security required. It’s important to note that combining the three factors should be distinct to maximize the security benefits.
3FA Protocols and Mechanisms
Several protocols and mechanisms support the implementation of 3FA—these range from standard protocols like OAuth and OpenID to specialized options for high-security environments.
Additionally, hardware tokens and biometric fingerprint scanners might be integrated into the system for the third factor.
The appropriate protocol authentication method and mechanism selection depends on various factors, including the organization’s existing infrastructure, user needs, authentication factors, and specific security requirements.
Benefits of 3FA

3FA offers many advantages, making it a worthy investment for organizations seeking robust security solutions. Not only does it dramatically reduce the chances of unauthorized access, but it also aligns well with various regulatory standards.
Improved Security Posture
Undoubtedly, the most significant benefit of 3FA is its enhanced security. By requiring three distinct verification forms to authenticate themselves before accessing accounts, 3FA makes it exponentially more challenging for unauthorized users to gain access. This is particularly beneficial for organizations handling sensitive data with high stakes for identity theft.
Regulatory Compliance
Another advantage of 3FA is its alignment with various regulatory standards. For organizations that must comply with guidelines such as GDPR, HIPAA, or PCI-DSS, implementing 3FA can aid in achieving and maintaining compliance. It is a tangible demonstration of an organization’s commitment to safeguarding user data.
User Experience and Usability
While adding more steps to the login process might seem like a burden, many modern 3FA solutions are designed with user experience in mind. Biometric authentication data, for instance, can be quicker and more natural to provide than entering a complex password. As a result, the additional security layer does not necessarily come at the expense of usability.
Implementing 3FA
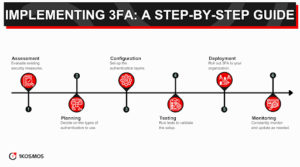
Technical Requirements
Implementing 3FA will inevitably require some technological adjustments. At a minimum, organizations must ensure they have the infrastructure to support this type of security measure. This could include software that supports multi-factor authentication protocols and hardware like biometric scanners or token generators.
A secure and reliable network is also essential for 3FA to function optimally. While cloud-based solutions are available, organizations must maintain network security protocols to minimize potential vulnerabilities.
Costs and Budgeting
The implementation of 3FA involves both upfront and ongoing costs. Upfront costs may include the purchase of hardware and software and the expenses related to system integration. Ongoing costs can encompass maintenance, updates, and possibly licensing fees.
Budgeting for 3FA should consider the direct costs and the potential savings from reduced security incidents. While the initial investment can be significant, the long-term benefits often justify the high level of expenditure.
Common Pitfalls and How to Avoid Them
While 3FA offers enhanced security, poor implementation can undermine its effectiveness. One common pitfall is inadequate training staff, leading to user errors that compromise safety. Proper training and awareness programs can mitigate this risk.
Another issue is over-reliance on one type of authentication or one authentication factor alone, such as using multiple biometric identifiers, which defeats the purpose of multi-factor authentication. A diversified approach using various types of authentication factors is recommended.
Potential Challenges and Criticisms
The Complexity Issue
One of the criticisms of 3FA is the added complexity it introduces. Critics argue that while the system is more secure than a one-time password, it becomes more cumbersome. However, many 3FA solutions focus on improving the user experience to mitigate this issue, and the benefits of heightened security often outweigh the downsides.
Reliance on Technology
Another concern is the heavy reliance on technology, such as smartphones or other biometric authentication devices, which could malfunction or be lost.
This reliance creates a potential weak link in the security chain. To counter this, backup options and alternative authentication methods should be part of any app or comprehensive 3FA strategy.
User Acceptance and Training
As with any new system, user acceptance is often a hurdle. People generally resist change, particularly regarding technology that requires them to alter their habits. Effective training and awareness programs can go a long way in facilitating smooth adoption.
Emerging Trends in 3FA
As the digital identity landscape evolves, so too does 3FA. One emerging trend is the integration of artificial intelligence to improve the efficiency and accuracy of the authentication process. Machine learning algorithms could, for example, analyze user behavior to provide a more dynamic and secure form of authentication.
Integrating more advanced biometrics and AI offers promising avenues for 3FA’s development. Beyond facial recognition, fingerprints, and iris scans, new forms of biometric data, such as heart rate or brainwave patterns, are being explored.
Blockchain technology has also been touted as a possible element in the future of 3FA. It offers the potential for decentralized authentication methods that are not only secure but also more user-friendly. The immutable nature of blockchain records can further enhance the security aspects of 3FA transactions.
To wrap it all up, 3FA offers a heightened level of security that is becoming increasingly essential in our digitalized world. The potential applications and benefits are vast, from government agencies to everyday internet users. While implementing 3FA involves a range of logistical and technological considerations, the upside in terms of cybersecurity makes it a worthy investment. If you’re committed to taking your organization’s digital security to the next level, don’t hesitate to contact our team today.
